There was a quite fresh discussion and no “how to ways” had been provided, but a way exists. Below is a Linux example.
a. You have installed and working Veracrypt software
b. You have an YubiKey and installed either YubiKey Personalization Tool or YubiKey Manager. Make sure you can run those software under average user account and YubiKey software can detect your Yubikey dongle properly
c. Also make sure you can run
# yubico-piv-tool -a status
and no error output is produced
d. Veracrypt can read Yubikey data via OpenSC. I can recommend to download OpenSC source code to build and install OpenSC library from scratch. Have a note OpenSC and therefore Veracrypt can’t write any information to Yubikey
e. Set the path to OpenSC library
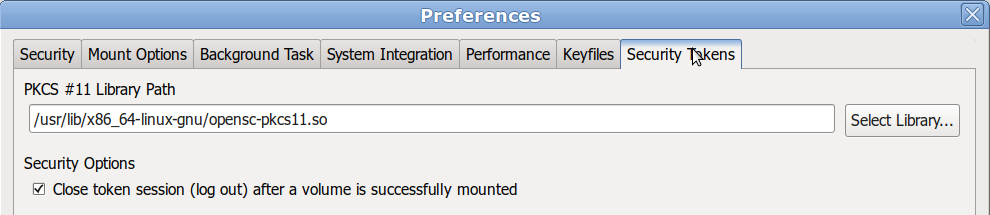
d. Generate and save a keyfile
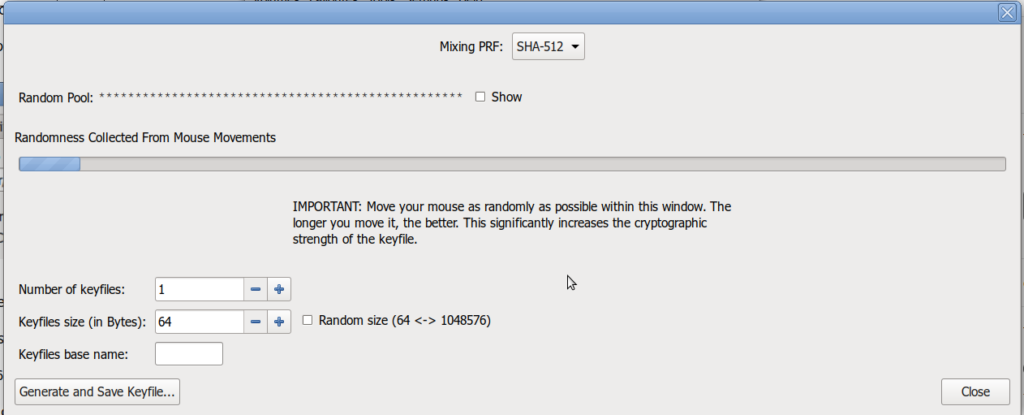
e. Convert the generated key file to the base64 formatted file
# base64 keyfile.dat > keyfile.dat.base64
g. Veracrypt detects valid following slots for Yubikey
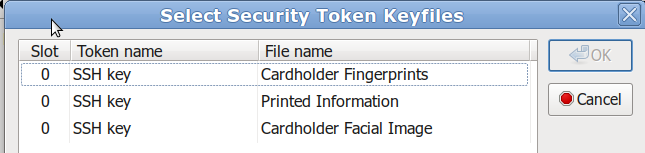
Let’s choose Cardholder Facial Image slot and find it’s ID. Refer to yubico-piv-tool
Supported PIV Object IDs
| Type of Object Data | ASN.1 OID | ID |
| Card Capability Container | 2.16.840.1.101.3.7.1.219.0 | 0x5fc107 |
| Card Holder Unique Identifier | 2.16.840.1.101.3.7.2.48.0 | 0x5fc102 |
| X.509 Certificate for PIV Authentication | 2.16.840.1.101.3.7.2.1.1 | 0x5fc105 |
| Cardholder Fingerprints | 2.16.840.1.101.3.7.2.96.16 | 0x5fc103 |
| Security Object | 2.16.840.1.101.3.7.2.144.0 | 0x5fc106 |
| Cardholder Facial Image | 2.16.840.1.101.3.7.2.96.48 | 0x5fc108 |
| X.509 Certificate for Card Authentication | 2.16.840.1.101.3.7.2.5.0 | 0x5fc101 |
| X.509 Certificate for Digital Signature | 2.16.840.1.101.3.7.2.1.0 | 0x5fc10a |
| X.509 Certificate for Key Management | 2.16.840.1.101.3.7.2.1.2 | 0x5fc10b |
| Printed Information | 2.16.840.1.101.3.7.2.48.1 | 0x5fc109 |
h. Let’s upload your keyfile to the Cardholder Facial Image slot with ID=0x5fc108
# yubico-piv-tool -a write-object -k --id 0x5fc108 -i keyfile.dat.base64 -f base64
Here you will be asked for your Yubikey’s management key and it’s a pity if you’ve lost it. No output errors mean keyfile is uploaded successfully.
Preparation part is done. Refer to the Veracrypt help how to use security token.
P.S.
Password extraction.
# pkcs11-tool -p yubikey-pin --application-id 2.16.840.1.101.3.7.2.96.48 --read-object --type data